Data Governance Policies: From Dusty Documents to Living Systems
How to create governance policies that people actually use and that drive business value
"We spent six months developing comprehensive data governance policies. We have a 200-page policy manual covering every conceivable scenario. It's been approved by legal, blessed by compliance, and published on our intranet. But somehow, nobody seems to know these policies exist, let alone follow them. Business users continue making the same data mistakes, and our governance issues persist. What's the point of having policies if they don't change behavior?"
This scenario plays out in organizations worldwide. Well-intentioned teams invest enormous effort creating detailed policy documents based on industry best practices and regulatory requirements. They follow established frameworks, incorporate lessons from other organizations, and produce impressive-looking policy manuals.
Yet these policies often become digital shelf-ware—comprehensive documents that exist in isolation from how people actually work with data.
The fundamental problem isn't that organizations lack policies. Most have too many policies that are too complex, too generic, and too disconnected from business workflows to be useful. They treat policy creation as a documentation exercise rather than a behavior change initiative.
The Traditional Approach: Create comprehensive policies that cover every possible scenario, ensure legal and compliance approval, publish them in a central repository, and expect people to read and follow them.
The Modern Reality: People need guidance at the point of decision-making, policies must be embedded in workflows, automation should enforce routine decisions, and policy evolution must keep pace with business change.
As data governance expert Robert Seiner notes in "Non-Invasive Data Governance," the most effective governance happens when "people don't even realize they're being governed." This principle applies especially to policies—the best policies are those that guide behavior without creating friction.
In this guide, we'll explore how to create data governance policies that actually work in modern organizations. We'll examine what makes policies effective, who should create them, how to implement them in ways people will actually use, and how to evolve from static documents to dynamic systems that adapt to changing business needs.
Why Data Governance Policies Exist: Beyond Compliance
Common Question: "Why do we need formal data governance policies? Can't we just rely on common sense and training?"
Understanding the fundamental purpose of data governance policies is essential for creating ones that actually work. The reasons go far beyond checking compliance boxes.
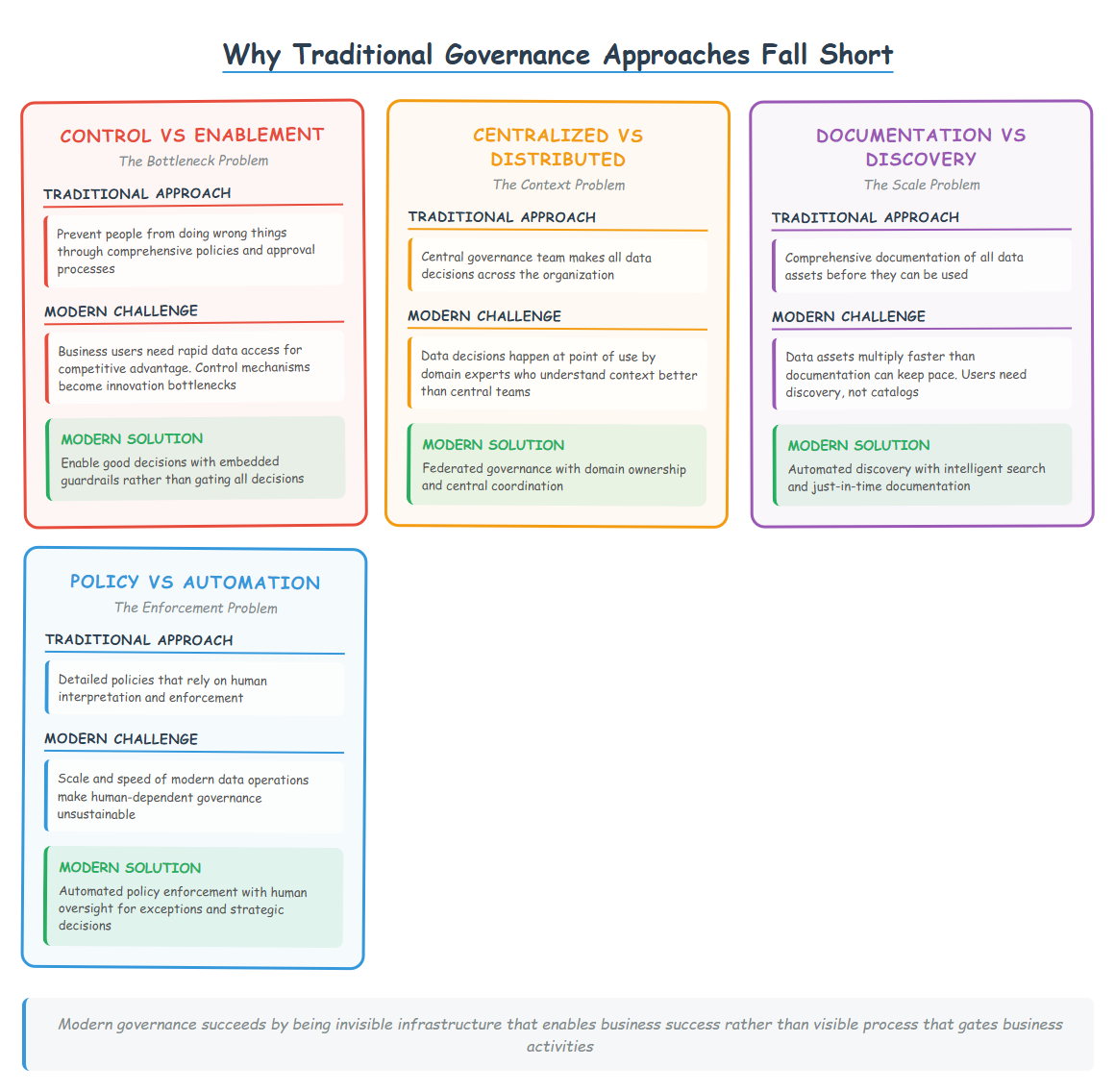
The Coordination Challenge
The Core Problem: Modern organizations have hundreds or thousands of people making data-related decisions daily. Without shared guidelines, these decisions are inconsistent, creating inefficiency, risk, and missed opportunities.
Example: Marketing wants to use customer data for personalization, Sales wants to share prospect data with partners, and Analytics wants to combine internal and external datasets. Without clear policies, each team makes decisions based on their understanding, creating inconsistent approaches to privacy, security, and quality.
As John Ladley explains in "Data Governance: How to Design, Deploy, and Sustain an Effective Data Governance Program," policies serve as "the mechanism by which an organization translates its data strategy into actionable guidance for daily operations."
The Scale Problem
Traditional Assumption: Senior leaders can make all important data decisions
Modern Reality: Data decisions happen too frequently and at too granular a level for centralized decision-making
Policy Solution: Enable distributed decision-making within established guardrails
The Consistency Problem
The Challenge: Different people interpret the same situation differently, leading to inconsistent approaches to data handling
Example: What constitutes "customer data"? Does it include prospect information? Anonymized behavioral data? Website visitor tracking? Without clear definitions and guidelines, different teams will interpret this differently.
The Risk Management Problem
Traditional View: Policies exist primarily to prevent bad things from happening
Modern View: Policies exist to enable good things to happen while managing appropriate risks
The shift is subtle but important. Modern data governance policies focus on enablement with appropriate controls rather than prevention with occasional exceptions.
The Learning and Adaptation Problem
The Challenge: Data environments change rapidly, but organizational learning about data governance happens slowly
Policy Solution: Capture institutional knowledge and best practices in reusable form while enabling continuous improvement
Traditional vs. Modern Policy Approaches
Common Question: "How should we approach policy creation differently in a modern data environment?"
The fundamental approach to data governance policies must evolve to match how modern organizations actually work with data.
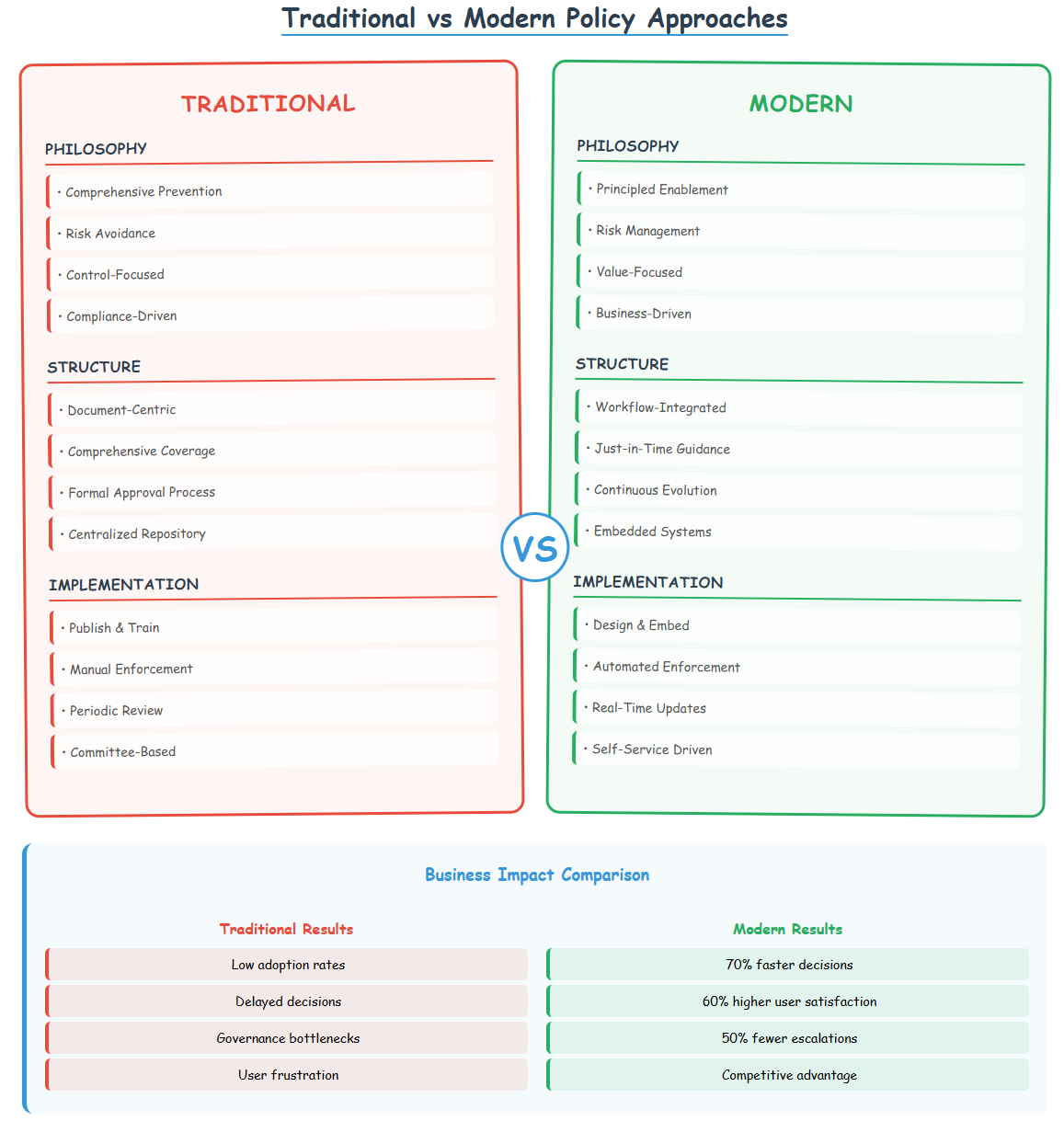
Philosophical Differences
Traditional: Comprehensive Prevention
Approach: Create detailed policies that anticipate every possible scenario and prevent all potential misuse
Problems:
- Impossible to anticipate every scenario in dynamic environments
- Comprehensive policies become too complex to understand or follow
- Focus on prevention inhibits innovation and business agility
- Creates adversarial relationship between governance and business teams
Modern: Principled Enablement
Approach: Establish clear principles and guidelines that enable good decisions while providing escalation paths for edge cases
Benefits:
- Principles scale to new scenarios without constant policy updates
- Focuses on enabling business value creation with appropriate controls
- Creates partnership between governance and business teams
- Adapts more easily to changing business needs
Structural Differences
Traditional: Document-Centric
Characteristics:
- Policies exist as standalone documents
- Comprehensive coverage of all scenarios
- Formal approval processes for any changes
- Centralized repositories (intranet, policy management systems)
- Assumption that people will read policies when needed
Modern: Workflow-Integrated
Characteristics:
- Policies embedded in business workflows and systems
- Just-in-time guidance at decision points
- Continuous evolution based on usage and feedback
- Accessible through the tools people already use
- Assumption that policies should be invisible when possible
Implementation Differences
Traditional: Publish and Train
Process:
- Write comprehensive policies
- Get legal and compliance approval
- Publish in central repository
- Conduct training sessions
- Expect compliance
Modern: Design and Embed
Process:
- Understand actual business workflows
- Design policy guidance for decision points
- Embed guidance in systems and processes
- Automate routine policy enforcement
- Measure behavior change and iterate
Maintenance Differences
Traditional: Periodic Review
Approach: Annual or biannual policy review cycles with formal update processes
Problems: Policies become outdated between review cycles, changes require extensive approval processes, updates are disruptive to business operations
Modern: Continuous Evolution
Approach: Continuous monitoring of policy effectiveness with agile update processes
Benefits: Policies stay current with business needs, changes can be implemented quickly, updates are seamless for business users
Who Should Write Data Governance Policies?
Common Question: "Who in our organization should be responsible for creating and maintaining data governance policies?"
The answer depends on your organizational model, but the most effective approach typically involves collaboration between multiple stakeholders rather than delegation to a single team.
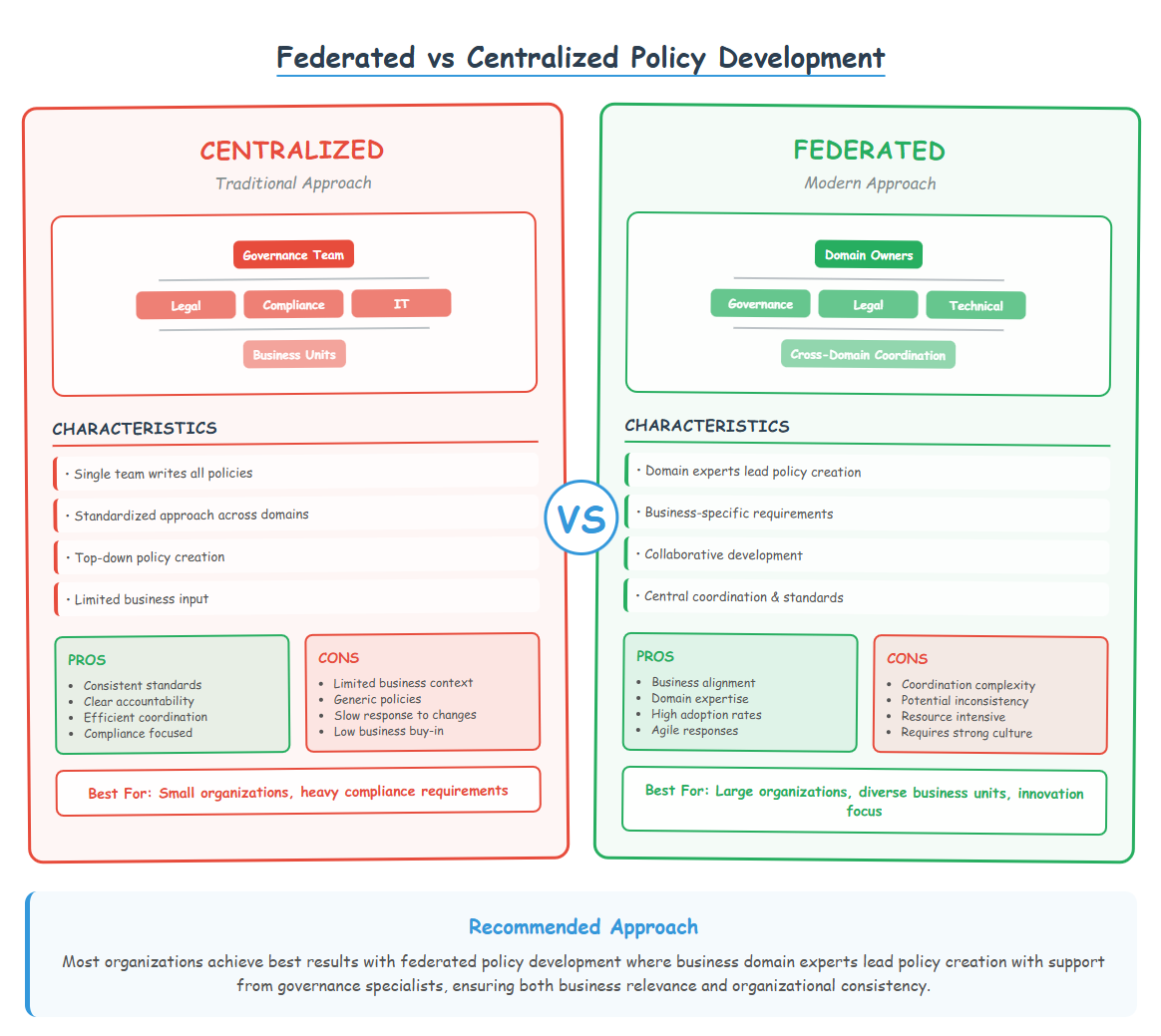
Traditional Approach: Central Policy Team
Typical Structure: Dedicated governance or compliance team writes all policies
Problems:
- Limited understanding of actual business workflows and needs
- Policies tend to be generic rather than business-specific
- Slow response to changing business requirements
- Limited buy-in from business teams who didn't participate in creation
Modern Approach: Federated Policy Development
Recommended Structure: Business domain experts lead policy development with support from governance specialists
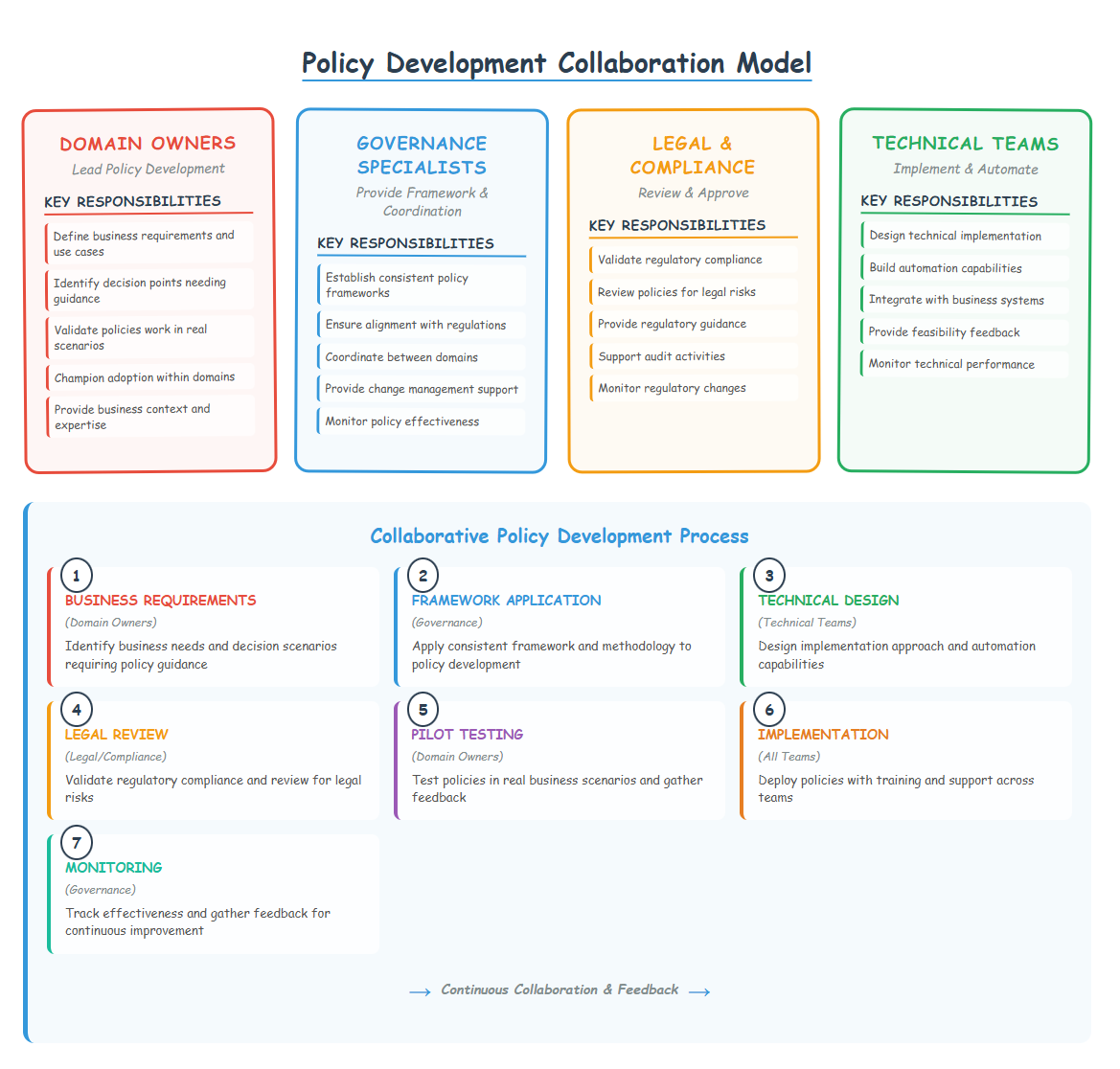
Business Domain Owners
Role: Lead policy development for their data domains Responsibilities:
- Define business requirements and use cases
- Identify decision points where guidance is needed
- Validate that policies work in actual business scenarios
- Champion policy adoption within their domains
Example: Customer Success team leads development of customer data usage policies because they understand customer interaction patterns and business requirements
Governance Specialists
Role: Provide framework, methodology, and cross-domain coordination Responsibilities:
- Establish consistent policy framework and templates
- Ensure policies align with regulatory requirements
- Coordinate between domains to prevent conflicts
- Provide change management and implementation support
Legal and Compliance
Role: Review and approve policies for regulatory compliance Responsibilities:
- Validate regulatory compliance requirements
- Review policies for legal risks
- Provide guidance on regulatory changes
- Support audit and compliance reporting
Technical Teams
Role: Implement policy automation and enforcement Responsibilities:
- Design technical implementation of policy enforcement
- Build automated policy monitoring and reporting
- Integrate policy guidance into business systems
- Provide feedback on technical feasibility
Collaboration Model
Policy Development Process:
- Business Requirements (Domain Owners): Identify business needs and decision scenarios
- Framework Application (Governance): Apply consistent framework and methodology
- Technical Design (Technical Teams): Design implementation and automation approach
- Legal Review (Legal/Compliance): Validate regulatory compliance
- Pilot Testing (Domain Owners): Test policies in real business scenarios
- Implementation (All Teams): Deploy policies with appropriate training and support
- Monitoring (Governance): Track effectiveness and gather feedback for improvement
What Should Be in Data Governance Policies?
Common Question: "What are the essential elements that every data governance policy should include?"
Effective data governance policies balance comprehensive guidance with practical usability. The key is including enough detail to enable good decisions without creating documents that are too complex to use.
Essential Policy Components
Policy Purpose and Scope
What: Clear statement of why the policy exists and what it covers Why Important: Helps people understand when to apply the policy and what outcomes it's designed to achieve Example: "This policy governs how customer personal data is collected, used, and shared to ensure privacy compliance while enabling personalized customer experiences."
Key Definitions
What: Business-friendly definitions of important terms and concepts Why Important: Ensures consistent understanding across different teams and functions Example: "Customer Data includes any information that can identify an individual customer or be linked to their account, including behavioral data and inferred preferences."
Guiding Principles
What: High-level principles that guide decision-making in scenarios not explicitly covered Why Important: Enables good decisions in new or edge-case scenarios without requiring policy updates Example: "When in doubt, choose the approach that best protects customer privacy while enabling legitimate business use."
Decision Framework
What: Step-by-step guidance for making common decisions Why Important: Provides practical guidance for routine decisions while maintaining consistency Example: "Before using customer data for a new purpose: 1) Verify consent covers the new use, 2) Assess privacy impact, 3) Implement appropriate technical controls, 4) Document the decision."
Roles and Responsibilities
What: Clear accountability for different aspects of policy implementation Why Important: Ensures someone is responsible for policy outcomes and provides escalation paths Example: "Marketing Data Steward approves new uses of customer data; Privacy Officer reviews high-risk scenarios; Legal approves external data sharing."
Escalation Procedures
What: Process for handling situations not covered by standard guidance Why Important: Provides path forward for edge cases without requiring policy violation Example: "Novel data use cases requiring legal review should be escalated to Privacy Officer within 2 business days."
Monitoring and Measurement
What: How policy effectiveness will be measured and monitored Why Important: Enables continuous improvement and demonstrates policy value Example: "Policy effectiveness measured by: time to resolve data use questions, privacy incident reduction, business user satisfaction."
What NOT to Include
Exhaustive Scenario Coverage: Attempting to address every possible scenario creates unwieldy documents that are difficult to maintain
Technical Implementation Details: Technical specifics belong in implementation guides, not business policies
Static Approval Lists: Lists of approved tools, vendors, or procedures become outdated quickly
Overly Prescriptive Procedures: Detailed step-by-step procedures that may not apply to all business contexts
The First 15 Essential Data Governance Policies
Common Question: "If we could only implement 15 data governance policies, which ones would have the biggest impact?"
Based on common governance challenges and regulatory requirements, here are the essential policies that most organizations should prioritize, with guidance on traditional vs. modern implementation approaches.
1. Data Classification and Sensitivity Policy
What It Is: Framework for categorizing data based on sensitivity and business importance
Why It Matters: Enables risk-appropriate handling of different data types without over-protecting low-risk data or under-protecting sensitive data
Who Needs to Know: Everyone who works with data
Traditional Approach: Comprehensive classification scheme with detailed criteria for each category
Modern Automation: Machine learning-powered classification with business-friendly labels and automated policy application
Example Categories: Public (marketing content), Internal (business metrics), Confidential (customer data), Restricted (financial records)
2. Data Access and Authorization Policy
What It Is: Guidelines for who can access what data under what circumstances
Why It Matters: Balances data security with business productivity by providing clear access frameworks
Who Needs to Know: All data users, data owners, IT security teams
Traditional Approach: Role-based access control with manual approval workflows
Modern Automation: Automated provisioning based on business role and data classification, with temporary access for specific projects
3. Data Quality Standards Policy
What It Is: Minimum acceptable quality standards for different types of business data
Why It Matters: Ensures data reliability for business decisions while avoiding perfectionism that delays business value
Who Needs to Know: Data stewards, business analysts, data engineers
Traditional Approach: Comprehensive quality metrics with manual monitoring and remediation
Modern Automation: Automated quality monitoring with self-healing capabilities and exception-based human intervention
4. Personal Data Privacy Policy
What It Is: Guidelines for handling personal data in compliance with privacy regulations
Why It Matters: Manages privacy compliance risk while enabling legitimate business use of personal data
Who Needs to Know: Anyone handling personal data, marketing teams, customer service
Traditional Approach: Detailed compliance procedures with manual privacy impact assessments
Modern Automation: Privacy-by-design technical controls with automated consent management and data minimization
5. Data Sharing and External Transfer Policy
What It Is: Framework for sharing data with external partners, vendors, and third parties
Why It Matters: Enables business partnerships and vendor relationships while managing data security and compliance risks
Who Needs to Know: Business development, procurement, legal, data owners
Traditional Approach: Contract-by-contract approval process with standard data protection clauses
Modern Automation: Automated partner onboarding with standard data sharing agreements and real-time monitoring
6. Data Retention and Disposal Policy
What It Is: Guidelines for how long to keep different types of data and how to securely dispose of it
Why It Matters: Manages storage costs and compliance obligations while preserving data needed for business operations
Who Needs to Know: Data stewards, IT operations, legal teams
Traditional Approach: Manual retention schedules with periodic review and deletion projects
Modern Automation: Automated lifecycle management with policy-driven retention and secure deletion
7. Data Backup and Recovery Policy
What It Is: Requirements for protecting data against loss and ensuring business continuity
Why It Matters: Protects against data loss while optimizing backup costs and recovery capabilities
Who Needs to Know: IT operations, business continuity teams, data owners
Traditional Approach: Comprehensive backup schedules with manual recovery testing
Modern Automation: Automated backup and recovery with business-driven recovery time objectives
8. Data Integration and Movement Policy
What It Is: Guidelines for moving data between systems while maintaining quality and security
Why It Matters: Enables data integration projects while preventing data corruption and security breaches
Who Needs to Know: Data engineers, IT architects, business analysts
Traditional Approach: Manual approval process for each data integration project
Modern Automation: Self-service data movement within policy guardrails with automated quality and security validation
9. Analytics and Reporting Policy
What It Is: Framework for creating and sharing business analytics while ensuring accuracy and appropriate access
Why It Matters: Promotes data-driven decision making while preventing misinterpretation and unauthorized access to sensitive insights
Who Needs to Know: Business analysts, data scientists, report consumers
Traditional Approach: Centralized analytics team with formal request and approval processes
Modern Automation: Self-service analytics platforms with embedded governance controls and automated insight validation
10. Data Documentation and Metadata Policy
What It Is: Requirements for documenting data sources, definitions, and business context
Why It Matters: Enables data discovery and appropriate use while reducing time spent searching for and understanding data
Who Needs to Know: Data stewards, business analysts, data engineers
Traditional Approach: Comprehensive documentation requirements with manual metadata entry
Modern Automation: Automated metadata harvesting with crowdsourced business context and AI-powered documentation
11. Data Incident Response Policy
What It Is: Procedures for responding to data quality issues, security breaches, and compliance violations
Why It Matters: Minimizes business impact from data incidents while ensuring appropriate stakeholder communication
Who Needs to Know: Data stewards, security teams, legal, business leaders
Traditional Approach: Formal incident response team with manual escalation procedures
Modern Automation: Automated incident detection and response with intelligent escalation based on business impact
12. Vendor and Third-Party Data Policy
What It Is: Framework for evaluating, onboarding, and managing external data sources and service providers
Why It Matters: Enables use of external data and services while managing vendor-related risks
Who Needs to Know: Procurement, legal, data stewards, business users of external data
Traditional Approach: Manual vendor assessment with standard contract requirements
Modern Automation: Automated vendor risk assessment with continuous monitoring of data quality and compliance
13. Data Experimentation and Innovation Policy
What It Is: Guidelines for using data in research, development, and experimental projects
Why It Matters: Enables innovation with data while managing risks associated with experimental use
Who Needs to Know: Data scientists, product managers, R&D teams
Traditional Approach: Project-by-project approval with comprehensive risk assessment
Modern Automation: Sandbox environments with automated controls and graduated risk management
14. Master Data Management Policy
What It Is: Framework for managing authoritative versions of critical business entities
Why It Matters: Ensures consistency of key business data across systems and processes
Who Needs to Know: Data stewards, business process owners, system administrators
Traditional Approach: Centralized master data team with manual data stewardship processes
Modern Automation: Federated master data management with automated synchronization and conflict resolution
15. Data Training and Literacy Policy
What It Is: Requirements and framework for data literacy training across the organization
Why It Matters: Ensures people have skills needed to work effectively and responsibly with data
Who Needs to Know: All employees, managers, HR teams
Traditional Approach: Formal training programs with periodic certification requirements
Modern Automation: Just-in-time training integrated into business workflows with adaptive learning based on role and usage patterns
Implementation Priority Framework
Immediate (Months 1-3): Data Classification, Access Authorization, Personal Data Privacy
Near-term (Months 3-9): Data Quality, External Sharing, Incident Response
Medium-term (Months 9-18): Integration, Analytics, Documentation
Long-term (Months 18+): Innovation, Master Data, Advanced Training
The key is implementing policies progressively based on business risk and value rather than trying to implement all policies simultaneously.
Where Policies Should Live: From Intranets to Integrated Systems
Common Question: "Where should we store and manage our data governance policies so people can actually find and use them?"
The location and accessibility of policies dramatically affects their adoption and effectiveness.
Traditional Approach: Central Repository
Common Locations:
- Company intranet policy sections
- Document management systems
- Compliance management platforms
- Shared network drives
Problems:
- Policies are divorced from business workflows
- People must remember to look for policies when making decisions
- Search and discovery is difficult
- Policies become outdated without regular review
- No integration with business systems
Modern Approach: Distributed and Integrated
Effective Locations:
Business Application Integration
Where: Embedded directly in the business applications where decisions are made
Benefits: Guidance available exactly when needed, integrated with business workflows
Example: Privacy guidance built into marketing automation platform when setting up new campaigns
Data Platform Integration
Where: Built into data discovery, preparation, and analysis tools
Benefits: Technical and business guidance available during data work
Example: Data quality standards and classification guidance integrated into data catalog
Self-Service Governance Portals
Where: Dedicated portals optimized for governance decision-making
Benefits: Comprehensive guidance with search, decision trees, and interactive tools
Example: Governance portal with role-based dashboards and context-sensitive guidance
Mobile and Field Access
Where: Mobile apps and offline-capable systems for remote workers
Benefits: Policy guidance available regardless of location or connectivity
Example: Field sales app with customer data handling guidance for client meetings
Collaboration Platforms
Where: Integrated with tools like Slack, Teams, or other collaboration platforms
Benefits: Policy guidance available in communication context
Example: Slack bot that provides instant policy guidance through conversational interface
Policy Management Architecture
Single Source of Truth
Concept: One authoritative source for each policy with syndication to point-of-use locations
Benefits: Ensures consistency while enabling distributed access
Implementation: Policy management system with APIs for integration
Version Control and Change Management
Concept: Software development practices applied to policy management
Benefits: Enables agile policy updates with appropriate review and rollback capabilities
Implementation: Git-based policy management with automated testing and deployment
Context-Aware Delivery
Concept: Different policy views and guidance based on user role, business context, and decision type
Benefits: Reduces information overload while ensuring relevant guidance is available
Implementation: Intelligent policy delivery system with user profiling and context detection
Analytics and Optimization
Concept: Continuous monitoring of policy usage and effectiveness
Benefits: Enables data-driven policy improvement and optimization
Implementation: Policy analytics platform with user behavior tracking and outcome measurement
Automation Opportunities: Making Policies Self-Executing
Common Question: "Which aspects of our governance policies can be automated, and how do we implement automation effectively?"
The most transformative aspect of modern data governance is the ability to automate routine policy enforcement, freeing humans to focus on strategic decisions and edge cases.
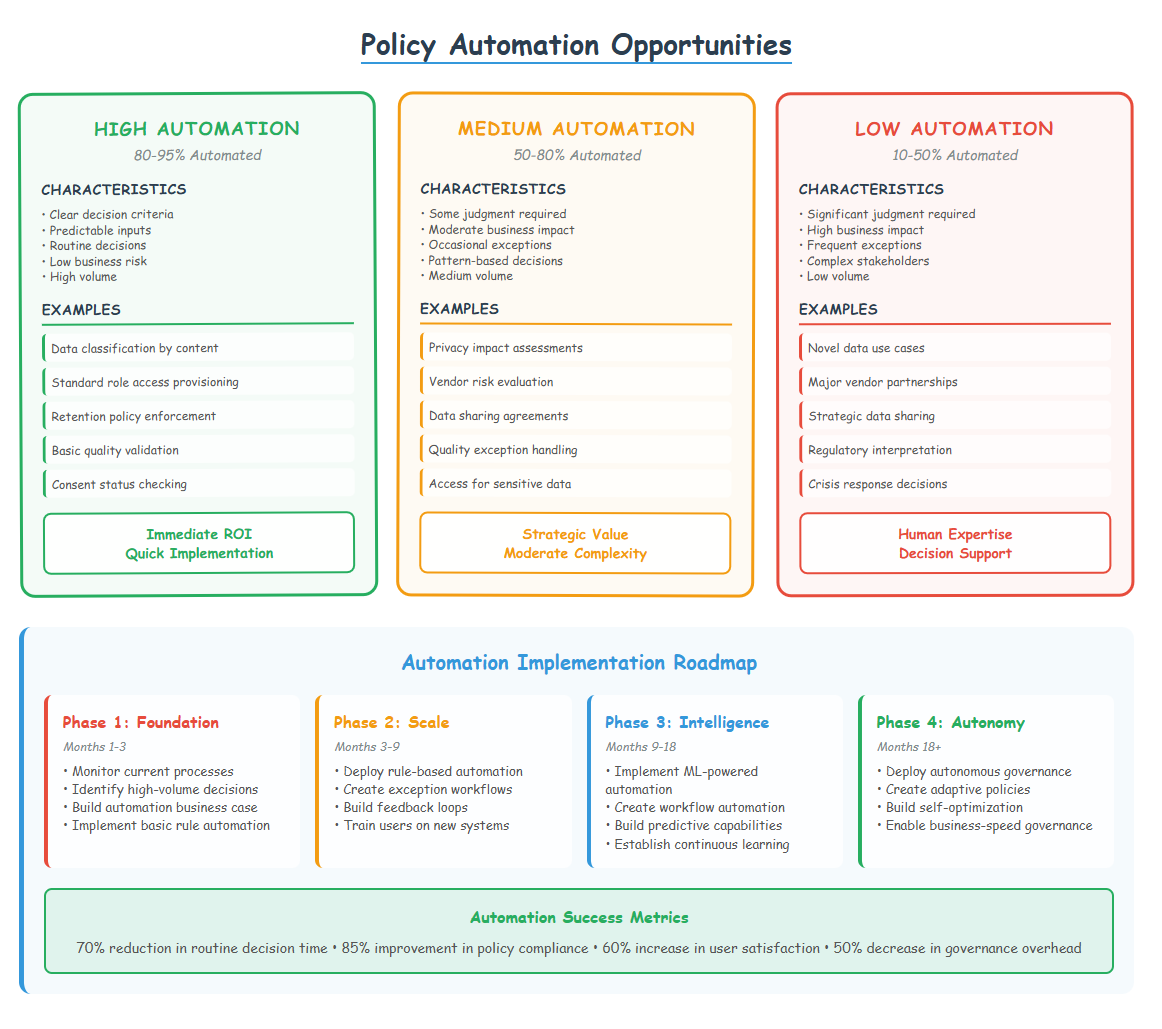
Automation Readiness Assessment
High Automation Potential
Characteristics: Clear decision criteria, predictable inputs, routine decisions, low business risk Examples: Data classification based on content patterns, access provisioning for standard roles, retention policy enforcement
Medium Automation Potential
Characteristics: Clear criteria with some judgment required, moderate business impact, occasional exceptions Examples: Data quality validation with business rule exceptions, privacy impact assessment for standard use cases
Low Automation Potential
Characteristics: Significant judgment required, high business impact, frequent exceptions, complex stakeholder involvement Examples: Novel data use case approval, major vendor partnerships, strategic data sharing decisions
Automation Implementation Strategies
Rule-Based Automation
What: Automate decisions based on pre-defined business rules and criteria Best For: Routine decisions with clear, consistent criteria Examples:
- Automatic data classification based on data source and content patterns
- Automated access grants for standard business roles
- Automatic data retention actions based on data age and type
Machine Learning-Powered Automation
What: Use AI to automate decisions based on patterns in historical decisions Best For: Complex decisions with consistent patterns but difficult-to-codify rules Examples:
- Intelligent data classification using content analysis
- Automated privacy risk assessment based on use case patterns
- Smart data quality scoring using multiple quality dimensions
Workflow Automation
What: Automate the process of policy application rather than the decisions themselves Best For: Multi-step processes with human decision points Examples:
- Automated routing of data access requests to appropriate approvers
- Orchestrated privacy impact assessment workflows
- Automated escalation of policy exceptions
Exception-Based Automation
What: Automate routine cases while flagging exceptions for human review Best For: Processes where most cases are routine but exceptions require judgment Examples:
- Automated vendor risk assessment with manual review for high-risk cases
- Self-service data access with escalation for sensitive data requests
- Automated data quality monitoring with alerts for significant issues
Implementation Framework
Phase 1: Monitor and Learn (Months 1-3)
- Implement monitoring of current manual processes
- Collect data on decision patterns and outcomes
- Identify highest-volume, lowest-risk automation opportunities
- Build business case for automation investment
Phase 2: Basic Rule Automation (Months 3-9)
- Implement simple rule-based automation for routine decisions
- Create exception handling processes for non-routine cases
- Establish feedback loops for automation improvement
- Train users on automated systems and exception processes
Phase 3: Intelligent Automation (Months 9-18)
- Implement machine learning-powered automation
- Create sophisticated workflow automation
- Build predictive capabilities for proactive governance
- Establish continuous learning and improvement processes
Phase 4: Autonomous Governance (Months 18+)
- Implement self-healing and self-optimizing governance systems
- Create adaptive policies that evolve based on business patterns
- Build comprehensive automation with human oversight
- Enable governance at the speed of business
Measuring Policy Effectiveness: Beyond Compliance Metrics
Common Question: "How do we measure whether our governance policies are actually working?"
Traditional governance programs focus heavily on compliance metrics—whether people are following policies. Modern governance requires measuring whether policies are enabling business success.
Traditional Metrics vs. Modern Metrics
Traditional Compliance-Focused Metrics
- Policy Acknowledgment Rate: Percentage of employees who have acknowledged policies
- Training Completion Rate: Percentage who have completed governance training
- Audit Compliance Score: Results from periodic compliance audits
- Policy Violation Count: Number of reported policy violations
Problems: These metrics measure process compliance but don't indicate whether policies are enabling business success or preventing real problems.
Modern Outcome-Focused Metrics
Business Enablement Metrics:
- Decision Velocity: Time from question to policy-guided decision
- Self-Service Success Rate: Percentage of governance questions resolved without escalation
- User Satisfaction: Business user satisfaction with policy guidance and processes
- Innovation Enablement: Speed of approving new data use cases and initiatives
Risk Management Metrics:
- Incident Prevention: Reduction in data-related business incidents
- Risk Detection Speed: Time from risk emergence to identification and mitigation
- Compliance Efficiency: Cost and time required for compliance activities
- Stakeholder Confidence: Executive and external stakeholder confidence in data practices
Value Creation Metrics:
- Business Value Enabled: Revenue or cost savings attributable to effective governance
- Competitive Advantage: Business capabilities enabled by trustworthy data practices
- Operational Efficiency: Process improvements resulting from clear governance guidance
- Strategic Alignment: Contribution of governance to overall business strategy success
Implementation Framework for Policy Measurement
Baseline Establishment
Measure Current State: Document current decision-making speed, user satisfaction, incident rates, and business outcomes before policy implementation
Identify Key Performance Indicators: Select 3-5 metrics that best reflect policy success for your organization
Establish Measurement Infrastructure: Implement systems to track metrics automatically where possible
Continuous Monitoring
Real-Time Dashboards: Create dashboards showing policy effectiveness metrics for different stakeholders
Regular Surveys: Conduct quarterly user satisfaction surveys focused on policy usefulness and accessibility
Business Impact Tracking: Monitor business outcomes that should improve with better governance
Periodic Deep Analysis
Quarterly Reviews: Detailed analysis of metric trends and correlation with business outcomes
Annual Assessment: Comprehensive review of policy effectiveness with stakeholder feedback and competitive benchmarking
Continuous Improvement: Use measurement results to identify policy improvement opportunities
The Future of Data Governance Policies
Common Question: "How will data governance policies need to evolve in the next few years?"
Understanding emerging trends helps organizations build policy frameworks that remain relevant as technology and business practices continue evolving.
Emerging Trends Affecting Policy Development
Data Contracts and Policy-as-Code
Trend: Data contracts that define data usage agreements as executable code rather than written policies Impact: Policies become enforceable through technical contracts between data producers and consumers Implementation: Smart contracts, API governance, and automated SLA enforcement
Conversational Policy Interfaces
Trend: Natural language interfaces that allow people to ask policy questions and receive contextual guidance Impact: Eliminates need to search through policy documents Implementation: AI chatbots with deep knowledge of organizational policies and business context
Data Mesh Governance Integration
Trend: Policies distributed to domain ownership with federated governance standards Impact: Domain-specific policies with enterprise coordination rather than centralized control Implementation: Domain-owned data products with embedded governance capabilities
Privacy-Preserving Policy Enforcement
Trend: Technical controls that enforce policies without exposing underlying data Impact: Strong privacy protection with business enablement Implementation: Homomorphic encryption, differential privacy, and federated learning technologies
Dynamic Policy Adaptation
Trend: Policies that automatically adjust based on changing business conditions and regulatory requirements Impact: Policies remain current without manual update cycles Implementation: Machine learning systems that monitor regulatory changes and business patterns
Building Future-Ready Policy Frameworks
Principle-Based Foundation: Focus on enduring principles rather than specific technologies or procedures
API-First Architecture: Design policies as services that can be consumed by any business application
Continuous Learning: Build feedback loops that enable policies to improve based on usage and outcomes
Human-AI Collaboration: Design for humans and AI systems working together on policy implementation
Conclusion: Policies as Living Systems
Effective data governance policies aren't documents—they're living systems that guide behavior, enable decisions, and adapt to changing business needs.
The transformation from traditional document-centric policies to modern workflow-integrated systems represents a fundamental shift in how organizations approach governance. Organizations that make this transition see compound returns: faster decision-making, better risk management, improved user satisfaction, and enhanced business agility.
The key insight: The best governance policies are those that people don't even notice—they become invisible infrastructure that enables business success rather than visible obstacles that gate business activities.
Your policy transformation starts with a simple question: "How can we provide the right guidance to the right people at the right time to enable the best possible decisions with data?"
Everything else builds from there.
Start building policies that work in practice, not just on paper. Your competitive advantage depends on it.